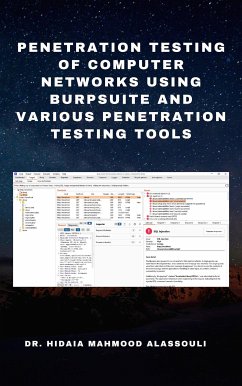
Hacking of Computer Networks (eBook, ePUB)
Full Course on Hacking of Computer Networks
Sofort per Download lieferbar
29,99 €
inkl. MwSt.

PAYBACK Punkte
0 °P sammeln!
The objective of the book is to summarize to the user with main topics in computer networking hacking. The book consists of the following parts: Part 1: Lab Setup Part2: Foot printing and Reconnaissance Part 3: Scanning Methodology Part 4: Enumeration Part 5:System Hacking Part 6: Trojans and Backdoors and Viruses Part 7: Sniffer and Phishing Hacking Part 8: Hacking Web Servers Part 9:Hacking Windows and Linux Systems Part 10: Wireless Hacking Part 11: Hacking Mobile Applications
The objective of the book is to summarize to the user with main topics in computer networking hacking.
The book consists of the following parts:
The book consists of the following parts:
- Part 1: Lab Setup
- Part2: Foot printing and Reconnaissance
- Part 3: Scanning Methodology
- Part 4: Enumeration
- Part 5:System Hacking
- Part 6: Trojans and Backdoors and Viruses
- Part 7: Sniffer and Phishing Hacking
- Part 8: Hacking Web Servers
- Part 9:Hacking Windows and Linux Systems
- Part 10: Wireless Hacking
- Part 11: Hacking Mobile Applications